
Cisco Releases Its Cloud Controls Framework To The Public
May 17, 2022
Support your remote access strategy with VDI
June 24, 2022What is DLP? How does it work? Why should we use it?
The DLP system is technically a system that keeps both the network and the clients under control.
DLP (Data Loss/Leak Prevention) is a relatively new type of data protection that is increasingly used in the field of network security. With DLP software, you can prevent unwanted data from your system or monitor the usage status of the files you specify. Although DLP installation requires an expert, the most important inputs for installation come from people who know and know the company. A single IT specialist cannot install DLP in a healthy and effective way. So there are some things you need to do before system integration.
The most important thing to decide before integrating DLP software into your system is what your valuable data is.

What are the Objectives of the DLP System?
The purpose of the security strategy, which is created by combining DLP techniques, is to keep records of the transactions made on the corporate data by examining who sent the data to where and in what way, and aims to prevent damages that may come from within the company. Knowing this, it encourages data users to be more careful. Thanks to DLP software, personal information security, copyright and industrial property rights and data visibility are secured.
DLP technology aims to protect data in its network, storage areas and end-user points. In this direction, data is handled in three different ways in DLP.
- Data in Motion is a type of data that moves within the network, that is, that is constantly in motion over transmission channels such as email, instant messaging, web and P2P.
- Data at Rest is a type of data that is sensitive to databases, file systems and other special storage units, which is used when necessary, and which is generally required to be protected in the first place.
- Data in Use: It is an active data type that is connected to sensitive and confidential data, although it is the type that the end user uses and processes constantly.
Why is DLP Important?
With the development of technology, it has become easier to access data. This has increased the data security problem. Many studies are carried out to restrict unauthorized access to data, to store and classify data, to determine access authorizations and to protect data against unwanted situations. Thanks to data loss prevention (DLP), unwanted data leakage from the system is prevented.
With DLP software, companies' critical data are safely stored. Thanks to the data loss prevention system, leakage of information and documents outside the institution is prevented. The operations on the data within the scope of the determined filters can be blocked if desired, and the process can be followed by only viewing if desired. In this process, data movements under control are recorded in the system memory. Reports are produced by the DLP software on issues such as incident response and forensic analysis. In this respect, DLP software is a must-have system to ensure information security.
What is DLP Working Logic?
DLP software is a little different from Antivirus or Firewall software.
DLP is a living system and if the information defined in the system is updated, new information must be added and data classifications and filters must be updated in case of system changes. Unlike DLP, standard definitions are made in Antivirus or Firewall software, and the problem can be intervened immediately by making software checks with automatic updates.
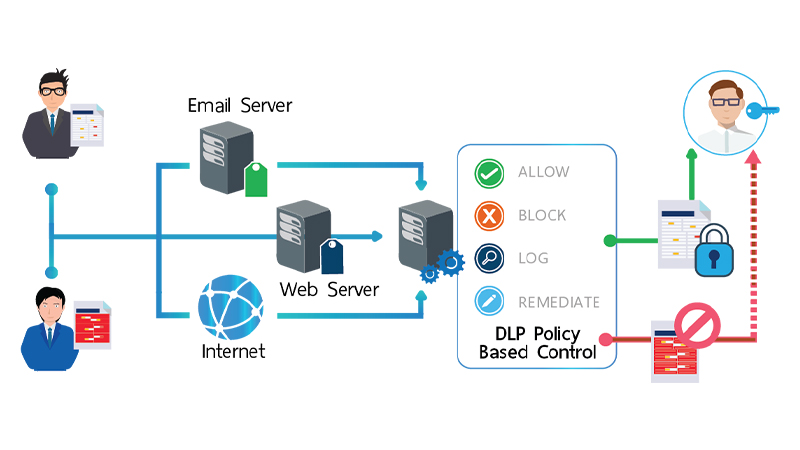
Necessary actions can be taken by detecting situations that conflict with the rules defined in DLP and incidents such as unauthorized access attempts, providing regular reporting and intervening when necessary.
Before starting the DLP Project, the classification structure should be established by determining the importance level of the data kept in the file system and databases. Each in-house department should determine the importance of the data it holds, and then this data should be introduced to the DLP system. All descriptions must be entered, as DLP does not know that these categories are critical or important.
The implementation of these systems; It requires studies such as planning controls such as reducing the risk, impact and degree of attack and ensuring the continuity of policies.
After you install the DLP software on your system, you should create symptom templates on the data and set up the DLP's responses when it encounters this data. For example, you can completely bypass the data in the first group, and you may not even keep any records about this data. This will make room for a significant reduction in system resources required by the DLP agent. You can make the data in the second group accessible only to users in the accounting department, and you can restrict access and change requests by other users. For the data in the third group, you can ensure the security of this data by defining the permissions such as writing, copying and printing only to the persons in the board of directors. The data in the fourth and last group can be completely closed to writing, copying, printing, moving, You can prevent any user from leaking, even if they take over the CEO's computer. The important thing here is to determine which data is priority for you, to specify them when making DLP settings, and to prepare special security templates for these data.
Unlike other security software, DLP is primarily designed to prevent internal damage. It is a known situation that hackers who attack large companies in an organized way primarily do social engineering and try to get information from within the company. In this case, how logical is it to unconditionally trust all employees inside multinational companies with hundreds or even thousands of employees? A malicious employee can leak data for an attack or easily copy your information without you knowing. This is where DLP comes into play , protecting your data against attacks from “unexpected places” .
What are the Usage Areas of DLP Software ?
With the sanctions of sectoral regulatory organizations, companies have been compelled to ensure data security. Regulatory sanctions such as Central Bank play an important role in taking serious steps regarding information security and therefore DLP.
Thanks to DLP, sensitive data is detected, classified and labeled. Data compatibility is also auditable with reporting support.
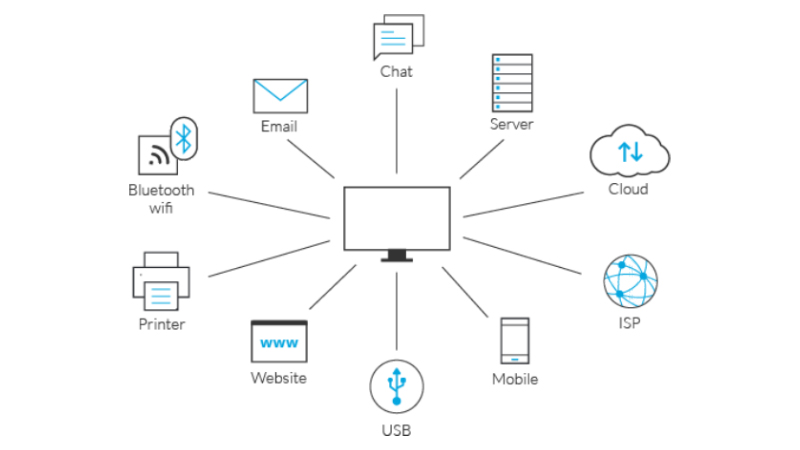
In line with the protection of the copyrights of the companies, the leakage of confidential information is prevented by making classifications thanks to DLP software.
With DLP software, all stored data of companies can be accessed by monitoring over endpoints, networks and the cloud. Thanks to DLP systems, how and how often users use data is monitored, and user behavior analysis is performed. Interactive data thus gains visibility.
Thanks to DLP software
- Restricting the use of USB and CD-DVD Roms to prevent data leakage
- Monitoring or blocking e-mails containing critical or important information
- Restricting file access
- Blocking copy/paste functions to prevent users from receiving data from within the application
- FTP restriction to prevent file upload
Some such rules are defined and necessary controls are provided.